Apple Inc. makes the latest version of its mobile operating system available for download today.
Most of the features of iOS 8 like HealthKit, the Family Sharing and Continuity features and Apple Pay, are consumer-focused.
However, IT departments around the globe will have to contend with iOS 8 pretty soon as iPhone and iPad users being loading the OS into their BYOD Apple devices.
Here are some things that IT administrators should keep in mind.
Privacy
With applications like the mobile payment app Apple Pay, the health tracking tool HealthKit and HomeKit which helps users communicate with connected accessories, IT departments will find more personal data in iOS 8 devices.
Online technology publication Computerworld.com suggests that IT shops review their mobility and BYOD policies to determine if they cover potential privacy and data protection issues that may crop up. Perhaps the human resources department should also be involved to ensure policies are compliant with federal, provincial and local laws, This could become critical especially when a company has an employee wellness program tied to corporate health insurance and tools like HealthKit may be collecting employee health data on a company or BYOD device
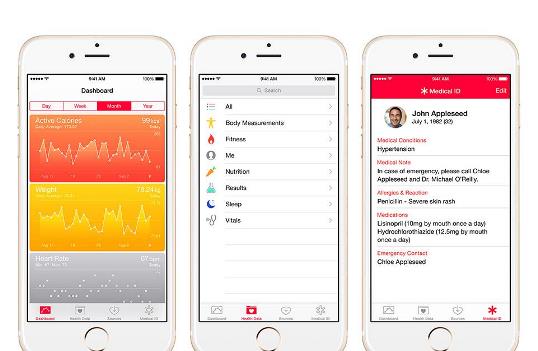
iOS 8 now allows apps to share functionality with other installed apps and even the operating system as well.
There are at list seven extension types that facilitate sharing of data between applications, over cloud or network storage.
IT departments should focus on these four:
Share – Allows users to share content via social networks and file sharing services
Document Picker – Allows apps to access and edit documents and content created by other applications. A document can be edited in one place by multiple apps without the app being copied or ported to the other apps.
Custom Action – Developers can create action buttons for iOS 8 Action Sheet that allows for applying watermarks on documents or translating text. The custom action might link apps and content to third-party services that might not be secure.
Location – Developers can designate a storage location which can be accessed by other apps. This could include cloud or network storage.

Touch ID is a highly secure system that basically functions as an alternative to passwords and login credentials. Apple has made it available for use by consumer app developers and enterprise app developers so the feature can be used to internal business apps.
IT departments however need to be wary of users installing third-party apps that also use the Touch ID feature. IT should determine is the third-party apps security features conflicts with the company`s enterprise mobile management authentication policies.

This system distinguishes applications downloaded by a user from the App Store (unmanaged apps) and those installed by IT using an enterprise app store or EMM (managed apps).
IT administrators can configure managed apps to share only specific types of information with other apps. IT can also prevent unmanaged sharing data.
User accounts like email accounts can also be managed and configured for instance to prevent the accounts from transferring content to unmanaged accounts or apps. iOS 8 also has a managed ebook feature which can be used by companies to push ePUB files and PDF to employees.

Users will be able to work with the document of their choice on the device of their choice. For example spreadsheets, images, PDFs and other documents can be accessed from iPhones, iPads, Mac machines and PCs.
IT may present some problems for IT because employees will likely be sharing company data between a company iPhone and a personal machine.
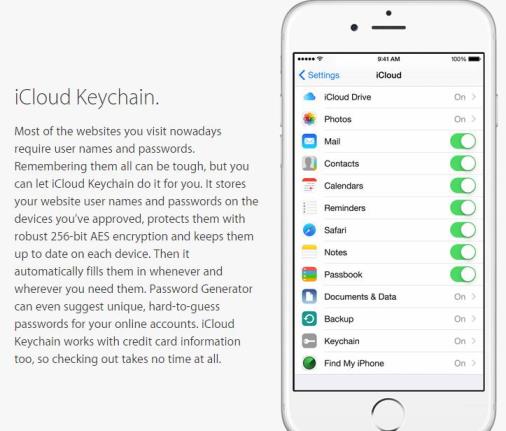
iOS 8 allows devices to automatically refresh Apple`s Kerberos-based single sign-on feature.
This enables users to work with corporate resources without re-authentication.
The S/MIME feature in iOS 8 encrypts individual messages. This is handy security option to activate for IT departments.
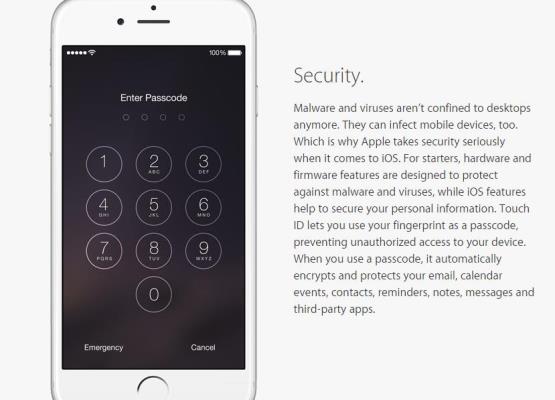
Apple has include new EMM options in iOS8. These include:
-Allow or prevent iCloud sync for managed apps
-Query devices to determine what ebooks are installed (this does not include personal ebooks)
-Query devices to determine when was latest backup using iCloud
-Prevention of iCloud backup
-Query device for iTunes account
For supervised devices (corporate purchased and configured devices):
-Allow or prevent access to Erase all Settings and Content function
-Allow or prevent users from configuring app and device restrictions thru the Settings
Also view our slideshow: Six alternatives to the iPhone 6


